Contents
- 1 1. Introduction to DNS and BIND 9
- 2 一、DNS与BIND简介 9
1. Introduction to DNS and BIND 9
一、DNS与BIND简介 9
转载来源:https://ftp.isc.org/isc/bind/cur/9.19/doc/arm/html/chapter1.html
The Internet Domain Name System (DNS) consists of: 互联网域名系统 (DNS) 包括:
- the syntax to specify the names of entities in the Internet in a hierarchical manner, 以分层方式指定 Internet 中实体名称的语法,
- the rules used for delegating authority over names, and 用于授权名称的规则,以及
- the system implementation that actually maps names to Internet addresses. 实际上将名称映射到 Internet 地址的系统实现。
DNS data is maintained in a group of distributed hierarchical databases. DNS 数据保存在一组分布式层次数据库中。
1.1. Scope of Document 1.1.文档范围
The Berkeley Internet Name Domain (BIND) software implements a domain name server for a number of operating systems. This document provides basic information about the installation and maintenance of Internet Systems Consortium (ISC) BIND version 9 software package for system administrators. Berkeley Internet Name Domain (BIND) 软件为许多操作系统实现了域名服务器。本文档为系统管理员提供有关安装和维护 Internet Systems Consortium (ISC) BIND 版本 9 软件包的基本信息。
This manual covers BIND version 9.19.13. 本手册涵盖 BIND 版本 9.19.13。
1.2. Organization of This Document 1.2.本文档的结构
Introduction to DNS and BIND 9 introduces the basic DNS and BIND concepts. Some tutorial material on The Domain Name System (DNS) is presented for those unfamiliar with DNS. A DNS Security Overview is provided to allow BIND operators to implement appropriate security for their operational environment. DNS 和 BIND 简介 9 介绍了基本的 DNS 和 BIND 概念。一些关于域名系统 (DNS) 的教程材料是为那些不熟悉 DNS 的人提供的。提供 DNS 安全概述以允许 BIND 操作员为其操作环境实施适当的安全性。
Resource Requirements describes the hardware and environment requirements for BIND 9 and lists both the supported and unsupported platforms. 资源要求描述了 BIND 9 的硬件和环境要求,并列出了支持和不支持的平台。
Configurations and Zone Files is intended as a quickstart guide for newer users. Sample files are included for Authoritative Name Servers (both primary and secondary), as well as a simple Resolver (Caching Name Servers) and a Forwarding Resolver Configuration. Some reference material on the Zone File is included. 配置和区域文件旨在作为新用户的快速入门指南。包含权威名称服务器(主要和次要)以及简单解析器(缓存名称服务器)和转发解析器配置的示例文件。包括有关区域文件的一些参考资料。
Name Server Operations covers basic BIND 9 software and DNS operations, including some useful tools, Unix signals, and plugins. 名称服务器操作涵盖基本的 BIND 9 软件和 DNS 操作,包括一些有用的工具、Unix 信号和插件。
Advanced Configurations builds on the configurations of Configurations and Zone Files, adding functions and features the system administrator may need. Advanced Configurations 建立在 Configurations 和 Zone Files 的配置之上,添加了系统管理员可能需要的功能和特性。
Security Configurations covers most aspects of BIND 9 security, including file permissions, running BIND 9 in a “jail,” and securing file transfers and dynamic updates. 安全配置涵盖了 BIND 9 安全的大部分方面,包括文件权限、在“监狱”中运行 BIND 9 以及保护文件传输和动态更新。
DNSSEC describes the theory and practice of cryptographic authentication of DNS information. The DNSSEC Guide is a practical guide to implementing DNSSEC. DNSSEC 描述了 DNS 信息的密码认证的理论和实践。 DNSSEC 指南是实施 DNSSEC 的实用指南。
Configuration Reference gives exhaustive descriptions of all supported blocks, statements, and grammars used in BIND 9’s named.conf configuration file. Configuration Reference 对 BIND 9 的 named.conf 配置文件中使用的所有受支持的块、语句和语法进行了详尽的描述。
Troubleshooting provides information on identifying and solving BIND 9 and DNS problems. Information about bug-reporting procedures is also provided. 故障排除提供了有关识别和解决 BIND 9 和 DNS 问题的信息。还提供了有关错误报告程序的信息。
Building BIND 9 is a definitive guide for those occasions where the user requires special options not provided in the standard Linux or Unix distributions. 在用户需要标准 Linux 或 Unix 发行版中未提供的特殊选项的情况下,Building BIND 9 是权威指南。
The Appendices contain useful reference information, such as a bibliography and historic information related to BIND and the Domain Name System, as well as the current man pages for all the published tools. 附录包含有用的参考信息,例如与 BIND 和域名系统相关的参考书目和历史信息,以及所有已发布工具的当前手册页。
1.3. Conventions Used in This Document 1.3.本文档中使用的约定
In this document, we generally use fixed-width text to indicate the following types of information: 在本文档中,我们一般使用 fixed-width 文字来表示以下几类信息:
- pathnames
- filenames
- URLs
- hostnames
- mailing list names 邮件列表名称
- new terms or concepts 新术语或概念
- literal user input 文字用户输入
- program output
- keywords
- variables
Text in “quotes,” bold text, or italics is also used for emphasis or clarity. “引号”中的文本、粗体文本或斜体也用于强调或清晰。
1.4. The Domain Name System (DNS) 1.4.域名系统 (DNS)
This is a brief description of the functionality and organization of the Domain Name System (DNS). It is provided to familiarize users with the concepts involved, the (often confusing) terminology used, and how all the parts fit together to form an operational system. 这是对域名系统 (DNS) 的功能和组织的简要描述。提供它是为了让用户熟悉所涉及的概念、使用的(通常令人困惑的)术语,以及所有部分如何组合在一起形成一个操作系统。
All network systems operate with network addresses, such as IPv4 and IPv6. The vast majority of humans find it easier to work with names rather than seemingly endless strings of network address digits. 所有网络系统都使用网络地址运行,例如 IPv4 和 IPv6。绝大多数人发现使用名称比使用看似无穷无尽的网络地址数字串更容易。 The earliest ARPANET systems (from which the Internet evolved) mapped names to addresses using a hosts file that was distributed to all entities whenever changes occurred. Operationally, such a system became rapidly unsustainable once there were more than 100 networked entities, which led to the specification and implementation of the Domain Name System that we use today. 最早的 ARPANET 系统(因特网由此演变而来)使用主机文件将名称映射到地址,只要发生更改,主机文件就会分发给所有实体。在操作上,一旦有超过 100 个联网实体,这样的系统就会迅速变得不可持续,这导致了我们今天使用的域名系统的规范和实施。
1.4.1. DNS Fundamentals 1.4.1. DNS 基础
The DNS naming system is organized as a tree structure comprised of multiple levels and thus it naturally creates a distributed system. Each node in the tree is given a label which defines its Domain (its area or zone) of Authority. The topmost node in the tree is the Root Domain; it delegates to Domains at the next level which are generically known as the Top-Level Domains (TLDs). They in turn delegate to Second-Level Domains (SLDs), and so on. The Top-Level Domains (TLDs) include a special group of TLDs called the Country Code Top-Level Domains (ccTLDs), in which every country is assigned a unique two-character country code from ISO 3166 as its domain. DNS 命名系统被组织为由多个级别组成的树结构,因此它自然地创建了一个分布式系统。树中的每个节点都被赋予一个标签,该标签定义了其权限域(其区域或区域)。树中最顶层的节点是根域;它委托给下一级的域,这些域通常称为顶级域 (TLD)。他们依次委托给二级域 (SLD),依此类推。顶级域 (TLD) 包括一组特殊的 TLD,称为国家代码顶级域 (ccTLD),其中每个国家都被分配了一个来自 ISO 3166 的唯一双字符国家代码作为其域。
Note
The Domain Name System is controlled by ICANN (https://www.icann.org) (a 501c non-profit entity); their current policy is that any new TLD, consisting of three or more characters, may be proposed by any group of commercial sponsors and if it meets ICANN’s criteria will be added to the TLDs. 域名系统由 ICANN ( https://www.icann.org )(501c 非营利实体)控制;他们目前的政策是,任何由三个或更多字符组成的新 TLD 都可以由任何商业赞助商团体提议,如果它符合 ICANN 的标准,将被添加到 TLD 中。
The concept of delegation and authority flows down the DNS tree (the DNS hierarchy) as shown: 授权和权限的概念在 DNS 树(DNS 层次结构)中向下流动,如下所示:
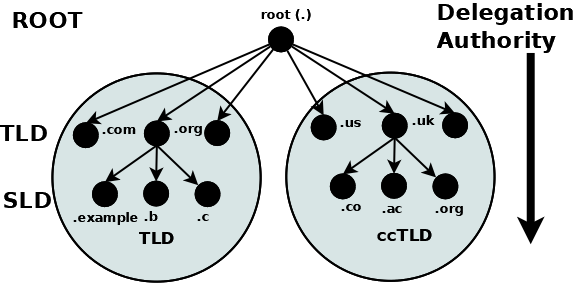
Delegation and Authority in the DNS Name Space DNS 名称空间中的委派和权限
A domain is the label of a node in the tree. A domain name uniquely identifies any node in the DNS tree and is written, left to right, by combining all the domain labels (each of which are unique within their parent’s zone or domain of authority), with a dot separating each component, up to the root domain. 域是树中节点的标签。域名唯一标识 DNS 树中的任何节点,并从左到右通过组合所有域标签(每个域标签在其父级区域或授权域内是唯一的)来编写,每个组件之间用一个点分隔,最多根域。 In the above diagram the following are all domain names: 在上图中,以下都是域名:
example.com
b.com
ac.uk
us
orgThe root has a unique label of “.” (dot), which is normally omitted when it is written as a domain name, but when it is written as a Fully Qualified Domain Name (FQDN) the dot must be present. Thus: 根有一个独特的标签“。” (点),当它写成域名时通常被省略,但当它写成完全限定域名 (FQDN) 时,点必须存在。因此:
example.com # domain name
example.com. # FQDN1.4.2. Authority and Delegation 1.4.2.授权与委托
Each domain (node) has been delegated the authority from its parent domain. The delegated authority includes specific responsibilities to ensure that every domain it delegates has a unique name or label within its zone or domain of authority, and that it maintains an authoritative list of its delegated domains. The responsibilities further include an operational requirement to operate two (or more) name servers (which may be contracted to a third party) which will contain the authoritative data for all the domain labels within its zone of authority in a zone file. Again, the tree structure ensures that the DNS name space is naturally distributed. 每个域(节点)都从其父域中获得授权。授权机构包括确保其授权的每个域在其区域或授权域内具有唯一名称或标签的特定责任,并确保其维护其授权域的权威列表。职责还包括运营两个(或更多)名称服务器(可能与第三方签约)的操作要求,这些名称服务器将在区域文件中包含其权限区域内所有域标签的权威数据。同样,树结构确保 DNS 名称空间是自然分布的。
The following diagram illustrates that Authoritative Name Servers exist for every level and every domain in the DNS name space: 下图说明了 DNS 名称空间中的每个级别和每个域都存在权威名称服务器:
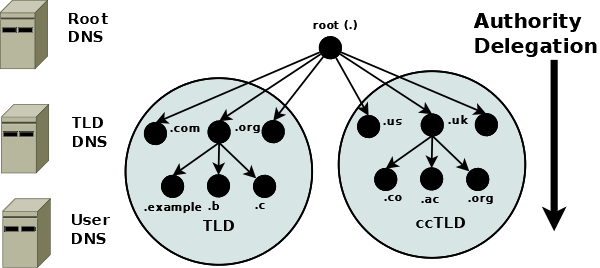
Authoritative Name Servers in the DNS Name Space DNS 名称空间中的权威名称服务器
Note
The difference between a domain and a zone can appear confusing. 域和区域之间的区别可能看起来令人困惑。 Practically, the terms are generally used synonymously in the DNS. If, however, you are into directed graphs and tree structure theory or similar exotica, a zone can be considered as an arc through any node (or domain) with the domain at its apex. 实际上,这些术语在 DNS 中通常作为同义词使用。但是,如果您对有向图和树结构理论或类似的奇异事物感兴趣,则可以将区域视为通过任何节点(或域)的弧,域位于其顶点。 The zone therefore encompasses all the name space below the domain. This can, however, lead to the concept of subzones and these were indeed defined in the original DNS specifications. Thankfully the term subzone has been lost in the mists of time. 因此,区域包含域下的所有名称空间。然而,这可能会引出子区域的概念,而这些确实在原始 DNS 规范中进行了定义。值得庆幸的是,subzone 这个词已经消失在时间的迷雾中。
1.4.3. Root Servers 1.4.3.根服务器
The root servers are a critical part of the DNS authoritative infrastructure. There are 13 root servers (a.root-servers.net to m.root-servers.net). The number 13 is historically based on the maximum amount of name and IPv4 data that could be packed into a 512-byte UDP message, and not a perverse affinity for a number that certain cultures treat as unlucky. 根服务器是 DNS 权威基础设施的重要组成部分。有 13 个根服务器(a.root-servers.net 到 m.root-servers.net)。历史上,数字 13 是基于可以打包到 512 字节 UDP 消息中的名称和 IPv4 数据的最大数量,而不是某些文化认为不吉利的数字的反常亲和力。 The 512-byte UDP data limit is no longer a limiting factor and all root servers now support both IPv4 and IPv6. In addition, almost all the root servers use anycast, with well over 300 instances of the root servers now providing service worldwide (see further information at https://www.root-servers.org). The root servers are the starting point for all name resolution within the DNS. 512 字节的 UDP 数据限制不再是限制因素,所有根服务器现在都支持 IPv4 和 IPv6。此外,几乎所有根服务器都使用任播,现在有超过 300 个根服务器实例在全球范围内提供服务(请参阅 https://www.root-servers.org 处的更多信息)。根服务器是 DNS 中所有名称解析的起点。
1.4.4. Name Resolution 1.4.4.名称解析
So far all the emphasis has been on how the DNS stores its authoritative domain (zone) data. 到目前为止,所有重点都放在 DNS 如何存储其权威域(区域)数据上。 End-user systems use names (an email address or a web address) and need to access this authoritative data to obtain an IP address, which they use to contact the required network resources such as web, FTP, or mail servers. 最终用户系统使用名称(电子邮件地址或网址)并需要访问此权威数据以获得 IP 地址,他们使用该地址联系所需的网络资源,例如 Web、FTP 或邮件服务器。 The process of converting a domain name to a result (typically an IP address, though other types of data may be obtained) is generically called name resolution, and is handled by resolvers (also known as caching name servers and many other terms). The following diagram shows the typical name resolution process: 将域名转换为结果(通常是 IP 地址,但可能会获得其他类型的数据)的过程通常称为名称解析,由解析器(也称为缓存名称服务器和许多其他术语)处理。下图显示了典型的名称解析过程:
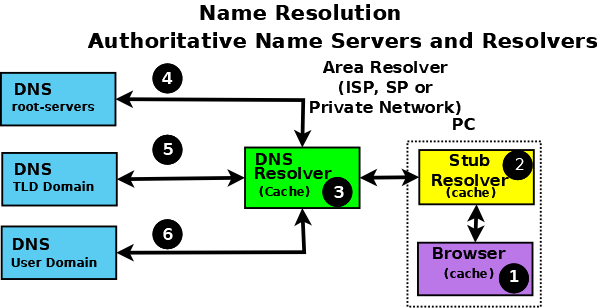
Authoritative Name Servers and Name Resolution 权威名称服务器和名称解析
An end-user application, such as a browser (1), when needing to resolve a name such as www.example.com, makes an internal system call to a minimal function resolution entity called a stub resolver (2). The stub resolver (using stored IP addresses) contacts a resolver (a caching name server or full-service resolver) (3), which in turn contacts all the necessary authoritative name servers (4, 5, and 6) to provide the answer that it then returns to the user (2, 1). 当需要解析 www.example.com 等名称时,最终用户应用程序(例如浏览器 (1))会对称为存根解析器 (2) 的最小功能解析实体进行内部系统调用。存根解析器(使用存储的 IP 地址)联系解析器(缓存名称服务器或全服务解析器)(3),后者又联系所有必要的权威名称服务器(4、5 和 6)以提供答案然后返回给用户 (2, 1)。 To improve performance, all resolvers (including most stub resolvers) cache (store) their results such that a subsequent request for the same data is taken from the resolver’s cache, removing the need to repeat the name resolution process and use time-consuming resources. 为了提高性能,所有解析器(包括大多数存根解析器)都缓存(存储)它们的结果,以便对相同数据的后续请求从解析器的缓存中获取,从而无需重复名称解析过程和使用耗时的资源。 All communication between the stub resolver, the resolver, and the authoritative name servers uses the DNS protocol’s query and response message pair. 存根解析器、解析器和权威名称服务器之间的所有通信都使用 DNS 协议的查询和响应消息对。
1.4.5. DNS Protocol and Queries 1.4.5. DNS 协议和查询
DNS queries use the UDP protocol over the reserved port 53 (but both TCP and TLS can optionally be used in some parts of the network). DNS 查询在保留的端口 53 上使用 UDP 协议(但在网络的某些部分可以选择使用 TCP 和 TLS)。
The following diagram shows the name resolution process expressed in terms of DNS queries and responses. 下图显示了以 DNS 查询和响应表示的名称解析过程。

Resolvers and Queries 解析器和查询
The stub resolver sends a recursive query message (with the required domain name in the QUESTION section of the query) (2) to the resolver. A recursive query simply requests the resolver to find the complete answer. A stub resolver only ever sends recursive queries and always needs the service of a resolver. The response to a recursive query can be: 存根解析器向解析器发送递归查询消息(在查询的问题部分中包含所需的域名)(2)。递归查询只是请求解析器找到完整的答案。存根解析器只发送递归查询,并且始终需要解析器的服务。对递归查询的响应可以是:
- The answer to the user’s QUESTION in the ANSWER section of the query response. 在查询响应的 ANSWER 部分中对用户问题的回答。
- An error (such as NXDOMAIN – the name does not exist). 错误(例如 NXDOMAIN – 名称不存在)。
The resolver, on receipt of the user’s recursive query, either responds immediately, if the ANSWER is in its cache, or accesses the DNS hierarchy to obtain the answer. The resolver always starts with root servers and sends an iterative query (4, 5, and 6). The response to an iterative query can be: 解析器收到用户的递归查询后,如果答案在其缓存中,则立即响应,或者访问 DNS 层次结构以获得答案。解析器始终从根服务器开始并发送迭代查询(4、5 和 6)。对迭代查询的响应可以是:
-
The answer to the resolver’s QUESTION in the ANSWER section of the query response. 查询响应的 ANSWER 部分中解析器问题的答案。
-
A referral (indicated by an empty ANSWER section but data in the AUTHORITY section, and typically IP addresses in the ADDITIONAL section of the response).
-
推荐(由空的 ANSWER 部分表示,但 AUTHORITY 部分中有数据,通常 IP 地址位于响应的 ADDITIONAL 部分中)。
-
An error (such as NXDOMAIN – the name does not exist). 错误(例如 NXDOMAIN – 名称不存在)。
If the response is either an answer or an error, these are returned immediately to the user (and cached for future use). If the response is a referral, the resolver needs to take additional action to respond to the user’s recursive query. 如果响应是答案或错误,这些将立即返回给用户(并缓存以备将来使用)。如果响应是引用,解析器需要采取额外的操作来响应用户的递归查询。
A referral, in essence, indicates that the queried server does not know the answer (the ANSWER section of the response is empty), but it refers the resolver to the authoritative name servers (in the AUTHORITY section of the response) which it knows about in the domain name supplied in the QUESTION section of the query. 引用本质上表示被查询的服务器不知道答案(响应的 ANSWER 部分为空),但它将解析器引用到它知道的权威名称服务器(在响应的 AUTHORITY 部分)在查询的问题部分提供的域名中。 Thus, if the QUESTION is for the domain name www.example.com, the root server to which the iterative query was sent adds a list of the .com authoritative name servers in the AUTHORITY section. The resolver selects one of the servers from the AUTHORITY section and sends an iterative query to it. Similarly, the .com authoritative name servers send a referral containing a list of the example.com authoritative name servers. This process continues down the DNS hierarchy until either an ANSWER or an error is received, at which point the user’s original recursive query is sent a response. 因此,如果问题是针对域名 www.example.com,则向其发送迭代查询的根服务器会在 AUTHORITY 部分添加 .com 权威名称服务器列表。解析器从 AUTHORITY 部分选择一个服务器并向其发送迭代查询。同样,.com 权威名称服务器发送包含 example.com 权威名称服务器列表的引用。此过程沿 DNS 层次结构向下继续,直到收到 ANSWER 或错误,此时用户的原始递归查询会收到响应。
Note
The DNS hierarchy is always accessed starting at the root servers and working down; there is no concept of “up” in the DNS hierarchy. 始终从根服务器开始并向下访问 DNS 层次结构; DNS 层次结构中没有“向上”的概念。 Clearly, if the resolver has already cached the list of .com authoritative name servers and the user’s recursive query QUESTION contains a domain name ending in .com, it can omit access to the root servers. 显然,如果解析器已经缓存了 .com 权威名称服务器列表,并且用户的递归查询 QUESTION 包含以 .com 结尾的域名,它可以忽略对根服务器的访问。 However, that is simply an artifact (in this case a performance benefit) of caching and does not change the concept of top-down access within the DNS hierarchy. 然而,这只是缓存的一个产物(在本例中是性能优势),并没有改变 DNS 层次结构中自上而下访问的概念。
The insatiably curious may find reading RFC 1034 and RFC 1035 a useful starting point for further information. 好奇心旺盛的人可能会发现阅读 RFC 1034 和 RFC 1035 是获取更多信息的有用起点。
1.4.6. DNS and BIND 9 1.4.6. DNS 和 BIND 9
BIND 9 is a complete implementation of the DNS protocol. BIND 9 can be configured (using its named.conf file) as an authoritative name server, a resolver, and, on supported hosts, a stub resolver. BIND 9 是 DNS 协议的完整实现。 BIND 9 可以配置(使用其 named.conf 文件)作为权威名称服务器、解析器,以及在支持的主机上的存根解析器。 While large operators usually dedicate DNS servers to a single function per system, smaller operators will find that BIND 9’s flexible configuration features support multiple functions, such as a single DNS server acting as both an authoritative name server and a resolver. 虽然大型运营商通常将 DNS 服务器专用于每个系统的单一功能,但小型运营商会发现 BIND 9 的灵活配置功能支持多种功能,例如单个 DNS 服务器同时充当权威名称服务器和解析器。
Example configurations of basic authoritative name servers and resolvers and forwarding resolvers, as well as advanced configurations and secure configurations, are provided. 提供了基本权威名称服务器和解析器和转发解析器的示例配置,以及高级配置和安全配置。
1.5. DNS Security Overview 1.5. DNS 安全概述
DNS is a communications protocol. All communications protocols are potentially vulnerable to both subversion and eavesdropping. It is important for users to audit their exposure to the various threats within their operational environment and implement the appropriate solutions. DNS 是一种通信协议。所有通信协议都可能容易受到破坏和窃听。对用户而言,重要的是审核他们在操作环境中面临的各种威胁并实施适当的解决方案。 BIND 9, a specific implementation of the DNS protocol, provides an extensive set of security features. The purpose of this section is to help users to select from the range of available security features those required for their specific user environment. BIND 9 是 DNS 协议的特定实现,提供了广泛的安全功能集。本节的目的是帮助用户从一系列可用的安全功能中选择其特定用户环境所需的安全功能。
A generic DNS network is shown below, followed by text descriptions. In general, the further one goes from the left-hand side of the diagram, the more complex the implementation. 下面显示了一个通用的 DNS 网络,后面是文本描述。一般来说,离图的左侧越远,实现就越复杂。
Note
Historically, DNS data was regarded as public and security was concerned, primarily, with ensuring the integrity of DNS data. DNS data privacy is increasingly regarded as an important dimension of overall security, specifically DNS over TLS. 历史上,DNS 数据被视为公共数据,安全性主要是确保 DNS 数据的完整性。 DNS 数据隐私越来越被视为整体安全的一个重要方面,特别是 DNS over TLS。
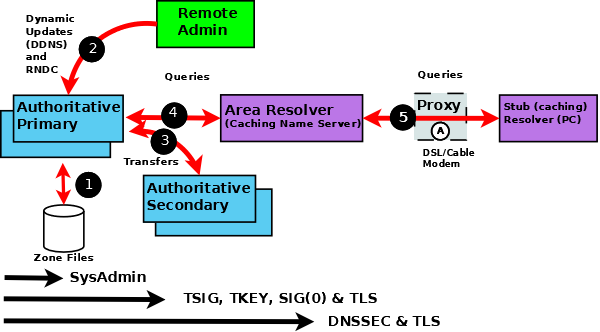
BIND 9 Security Overview BIND 9 安全概述
The following notes refer to the numbered elements in the above diagram. 以下注释涉及上图中的编号元素。
-
A variety of system administration techniques and methods may be used to secure BIND 9’s local environment, including file permissions, running BIND 9 in a jail, and the use of Access Control Lists.
-
可以使用多种系统管理技术和方法来保护 BIND 9 的本地环境,包括文件权限、在监狱中运行 BIND 9 以及访问控制列表的使用。
-
The remote name daemon control (rndc) program allows the system administrator to control the operation of a name server. The majority of BIND 9 packages or ports come preconfigured with local (loopback address) security preconfigured. If
rndcis being invoked from a remote host, further configuration is required. Thensupdatetool uses Dynamic DNS (DDNS) features and allows users to dynamically change the contents of the zone file(s).nsupdateaccess and security may be controlled usingnamed.confstatements or using TSIG or SIG(0) cryptographic methods. Clearly, if the remote hosts used for eitherrndcor DDNS lie within a network entirely under the user’s control, the security threat may be regarded as non-existent. Any implementation requirements, therefore, depend on the site’s security policy. -
远程名称守护程序控制 (rndc) 程序允许系统管理员控制名称服务器的操作。大多数 BIND 9 包或端口都预先配置了本地(环回地址)安全性。如果从远程主机调用
rndc,则需要进一步配置。nsupdate工具使用动态 DNS (DDNS) 功能并允许用户动态更改区域文件的内容。nsupdate访问和安全性可以使用named.conf语句或使用 TSIG 或 SIG(0) 加密方法来控制。显然,如果用于rndc或 DDNS 的远程主机位于完全由用户控制的网络中,则可以认为安全威胁不存在。因此,任何实施要求都取决于站点的安全策略。 -
Zone transfer from a primary to one or more secondary authoritative name servers across a public network carries risk. The zone transfer may be secured using
named.confstatements, TSIG cryptographic methods or TLS. Clearly, if the secondary authoritative name server(s) all lie within a network entirely under the user’s control, the security threat may be regarded as non-existent. Any implementation requirements again depend on the site’s security policy. -
通过公共网络从主要到一个或多个次要权威名称服务器的区域传输存在风险。可以使用
named.conf语句、TSIG 加密方法或 TLS 来保护区域传输。显然,如果二级权威名称服务器都位于完全由用户控制的网络中,则可以认为安全威胁不存在。任何实施要求再次取决于站点的安全策略。
If the operator of an authoritative name server (primary or secondary) wishes to ensure that DNS responses to user-initiated queries about the zone(s) for which they are responsible can only have come from their server, that the data received by the user is the same as that sent, and that non-existent names are genuine, then DNSSEC is the only solution. DNSSEC requires configuration and operational changes both to the authoritative name servers and to any resolver which accesses those servers. 如果权威名称服务器(主要或次要)的运营商希望确保 DNS 对用户发起的关于他们负责的区域的查询的响应只能来自他们的服务器,那么用户收到的数据与发送的相同,并且不存在的名称是真实的,那么 DNSSEC 是唯一的解决方案。 DNSSEC 需要对权威名称服务器和访问这些服务器的任何解析器进行配置和操作更改。
- The typical Internet-connected end-user device (PCs, laptops, and even mobile phones) either has a stub resolver or operates via a DNS proxy. A stub resolver requires the services of an area or full-service resolver to completely answer user queries.
- 典型的互联网连接终端用户设备(个人电脑、笔记本电脑,甚至手机)要么具有存根解析器,要么通过 DNS 代理运行。存根解析器需要区域或全服务解析器的服务来完全回答用户查询。
Stub resolvers on the majority of PCs and laptops typically have a caching capability to increase performance. At this time there are no standard stub resolvers or proxy DNS tools that implement DNSSEC. 大多数 PC 和笔记本电脑上的存根解析器通常具有缓存功能以提高性能。目前还没有实现 DNSSEC 的标准存根解析器或代理 DNS 工具。 BIND 9 may be configured to provide such capability on supported Linux or Unix platforms. DNS over TLS may be configured to verify the integrity of the data between the stub resolver and area (or full-service) resolver. BIND 9 可以配置为在受支持的 Linux 或 Unix 平台上提供此类功能。 DNS over TLS 可以配置为验证存根解析器和区域(或全服务)解析器之间数据的完整性。 However, unless the resolver and the Authoritative Name Server implements DNSSEC, end-to-end integrity (from authoritative name server to stub resolver) cannot be guaranteed. 但是,除非解析器和权威名称服务器实施 DNSSEC,否则无法保证端到端完整性(从权威名称服务器到存根解析器)。
发表回复